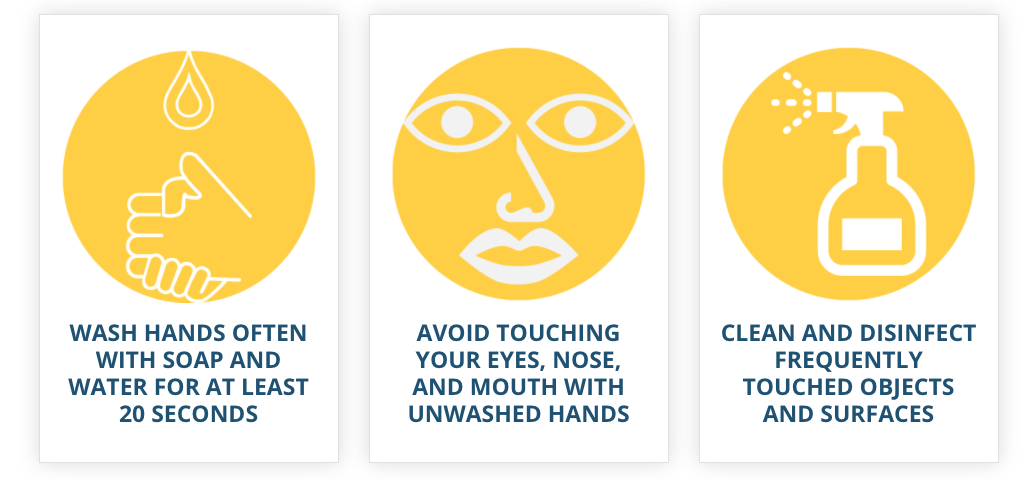
9 Key Elements of a Data Security Policy
While the conversation around the water cooler may be about the latest cyber breach, protecting your data against cyber attacks requires much more than words. Walk the talk to help protect your data with a documented data security policy.
Every employee needs to understand his or her obligation to protect company data. Employees also need clear expectations about behavior when it comes to their interaction with data. For that to happen, your data security policy needs to be published, understandable and enforceable. It should outline practices that help safeguard employee, customer, company and third-party business data and sensitive information.
As with many complex programs that deal with sophisticated products or topics, there are usually essential elements that form the foundation of a plan.
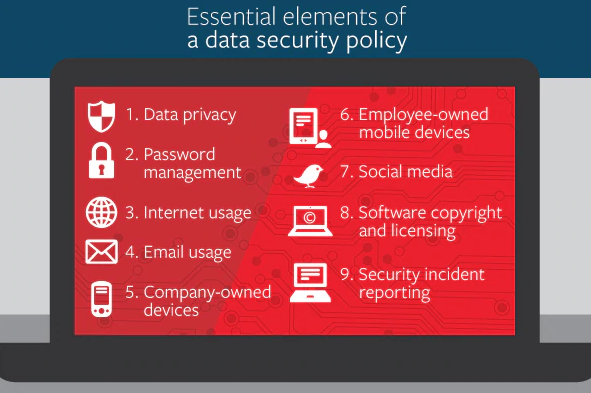
Essential Elements of a Data Security Policy
- Safeguard Data Privacy: Employees must understand that your privacy policy is a pledge to your customers that you will protect their information. Data should only be used in ways that will keep customer identity and the confidentiality of information secure. Of course, your employees and organizations must conform to all applicable laws and regulations.
- Establish Password Management: A password policy should be established for all employees or temporary workers who will access corporate resources. In general, password complexity should be established according to the job functions and data security requirements. Passwords should never be shared.
- Govern Internet Usage: Most people use the internet without a thought to the harm that can ensue. Employee misuse of the internet can place your company in an awkward, or even illegal, position. Establishing limits on employee internet usage in the workplace may help avoid these situations. Every organization should decide how employees can and should access the web. You want employees to be productive, and this may be the main concern for limiting internet usage, but security concerns should also dictate how internet guidelines are formulated.
- Manage Email Usage: Many data breaches are a result of employee misuse of email that can result in the loss or theft of data and the accidental downloading of viruses or other malware. Clear standards should be established regarding use of emails, message content, encryption and file retention.
- Govern and Manage Company-Owned Mobile Devices: When organizations provide mobile devices for their employees to use, a formal process should be implemented to help ensure that mobile devices are secure and used appropriately. Requiring employees to be responsible for protecting their devices from theft and requiring password protection in accordance with your password policy should be minimum requirements. Read More