Four Steps to Safer Drivers
If you want a safe fleet, start with safe drivers.
Studies have shown, again and again, that your drivers are your largest exposure to risk.1 And your risks are all over the map, literally.

Four Steps to Help Identify Safer Drivers
1. Check the MVR (Motor Vehicle Record)
Every driver comes with a history.
- Obtain MVRs for anyone who drives on behalf of your company.
- Review MVRs regularly to be sure they meet your standards.
- Apply your MVR policy consistently with all driving employees.
2. Monitor Driver Performance
You hire and train the best drivers possible, but you cannot be with your drivers all the time.
- Review all accidents and incidents.
- Conduct ride-along evaluations.
- Keep track of motorist call-in reports.
- Check vehicle performance data from engine computers and telematics devices to find evidence of speed, aggressive acceleration, hard braking and cornering.
- Review Department of Transportation (DOT) roadside inspection reports.
3. Prevent Driver Fatigue
Even the best driver gets tired. Fatigue is natural, and we all need regular rest to recharge our batteries. The National Highway Traffic Safety Administration estimates that approximately 100,000 accidents reported every year are due to driver fatigue.2
- Create policy and work schedules that mirror safety regulations on fatigue management.
- Provide training on the dangers of driving while fatigued.
- Manage work schedules and monitor hours of all drivers, even those who work from home, or at remote locations.
- Require drivers who are operating regulated commercial vehicles to adhere to applicable rules.
- Establish a written policy that specifies when employees must use a hotel or similar accommodations to rest.
- Be sure all drivers understand the signs of fatigue disorder, and encourage drivers with signs of a sleep disorder to consult with their doctor. Read More
6 Considerations Before Joining a Nonprofit Board
It may be the last thing you are thinking about when you volunteer on the board of a nonprofit, but are you aware you might be putting your personal assets at risk? The reason for that is nonprofits face many of the same threats as for-profit businesses, including the potential for lawsuits. If the nonprofit is sued and lacks the proper planning and protection, you could lose your savings, your home and other assets.
Nearly two out of three nonprofits reported a Directors & Officers liability claim within the past 10 years.1 These lawsuits can be brought by donors, vendors, competitors, employees, government regulators and others, and they are not limited to suing the nonprofit organization. As a member of the board, you could also be sued personally, and be responsible for the cost of hiring your own attorney to defend yourself.
“Serving on a nonprofit board can be a commitment of your time, talent and treasure,” says Thomas Herendeen, Non-Profit D&O Product Manager for Travelers. “You’ll want to take the time to understand the nonprofit’s mission, how it operates and whether you might have any conflicts of interest before you decide to join a board.”
Asking a few questions in advance can help you protect your personal assets, while also helping to ensure that the nonprofit has the strong board governance procedures and the proper coverage in place to protect its mission.
Following are six things to consider before you join a nonprofit board.
1. What’s expected of you as a board member?
Learn what other board members will expect of you, such as:
- Are there specific governance responsibilities?
- What is the time commitment and how many meetings does the nonprofit hold?
- Are you expected to fundraise on behalf of the group?
2. Who else sits on the board of directors?
- Who chairs the board? Consider meeting with the chairperson before committing to the board.
- What is his or her leadership style? Is the board committed to effective governance?
- Attend a board meeting before you commit to joining the board.
3. Does the organization have employees?
- If so, does the organization have an employee handbook and other written employment policies and procedures?
- Are managers and employees trained to make sure that they comply with employment laws?
- Are personnel decisions centralized and made by human resource professionals? Read more
How Does Cyber Insurance Work?

The cost of dealing with a data breach goes beyond repairing databases, strengthening security procedures or replacing lost laptops. Regulations requiring notifications of affected customers also drive costs for companies in which a data breach compromises personal or confidential data. Traditional business insurance may not be enough to protect companies from cyber-crime. But just how does cyber insurance work?
Typically, there are a number of different coverages available. To have the coverage that is right for your company, you and your agent can work together to tailor the coverages based on the specific risks your business faces. Following are some explanations of typical elements of a Travelers cyber insurance policy.
Third-Party (liability) and First-Party Coverage
What it does: Companies have an obligation to keep their customers’ protected health information (PHI) and personally identifiable information (PII) confidential. They may face potential liability if the information is exposed in a data breach. This coverage protects companies for liability to others and reimburses companies for expenses related to a data breach, which could include legal counsel and defense, a digital forensics team, notification costs, crisis communications and setting up a call center and credit monitoring for those affected by the data breach.
Why it’s important: Many companies store their customers’ confidential information, PHI and PII, as well as confidential corporate information, either for themselves or for another company. For example, an employee benefits company may have personnel records for the employees of dozens of companies it serves, which can mean that a single breach presents the potential for significant liability.
Worldwide Coverage
What it does: Claims and events can occur anywhere in the world, and notification requirements differ by location. To help fulfill these requirements, policyholders can access Travelers’ network of forensics, crisis communications and legal experts to address claims made or events occurring anywhere in the world.
Why it’s important: If a company has a data breach, it must follow the privacy laws that govern where its customers live, not just where it is headquartered. This can be costly, confusing and time-consuming for a company without specialized resources. Read more
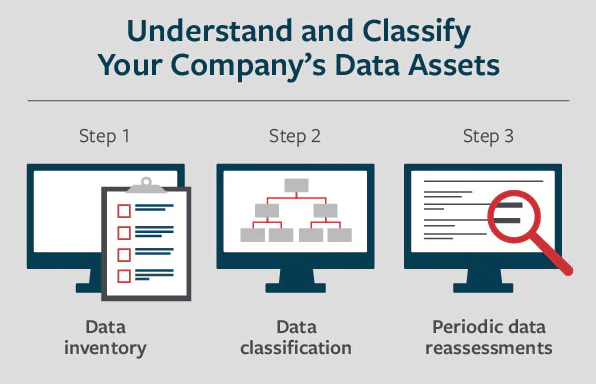
3 Steps for Data Assessment, Inventory & Classification
Know Your Data and How to Protect It.
Because businesses and organizations collect many different types of information, to help quantify their cyber security risk exposures, companies should first understand the types of information they are collecting, storing and sharing. This information can range in complexity from a simple inventory of products to personal information, including private health and financial records. Personal and customer information may be subject to federal, state and local regulations, Payment Card Industry standards, or perhaps foreign privacy standards.
While having a data security policy is the first step to help protect your data, the next logical step is to inventory all the data you handle during the course of business. This can help you classify it based on its confidentiality to determine who should be authorized to access it and to determine the level of data security needed.
What Kind of Data are You Handling?
Here is a three-step process that can help companies understand and classify their various data assets.
Step 1: Data Inventory
Determine the type of data you store.
- Personally Identifiable Information: Often referred to as PII, this information may include such things as first and last names, home or business addresses, email addresses, credit card and bank account numbers, taxpayer identification numbers, medical records and Social Security numbers. It also may include gender, age, date of birth, city of birth or residence, driver’s license number, and phone numbers.
- Customer information: This may include payment information such as payment card numbers and verification codes, billing and shipping addresses, email addresses, phone numbers, and purchasing history, among other data.
- Intellectual property: This may include proprietary and sensitive business information such as financial records, product designs, human resource records and internal correspondence and reports. It also can include intellectual property of others with whom you have a business relationship, including customers and vendors. Read More
9 Key Elements of a Data Security Policy
While the conversation around the water cooler may be about the latest cyber breach, protecting your data against cyber attacks requires much more than words. Walk the talk to help protect your data with a documented data security policy.
Every employee needs to understand his or her obligation to protect company data. Employees also need clear expectations about behavior when it comes to their interaction with data. For that to happen, your data security policy needs to be published, understandable and enforceable. It should outline practices that help safeguard employee, customer, company and third-party business data and sensitive information.
As with many complex programs that deal with sophisticated products or topics, there are usually essential elements that form the foundation of a plan.
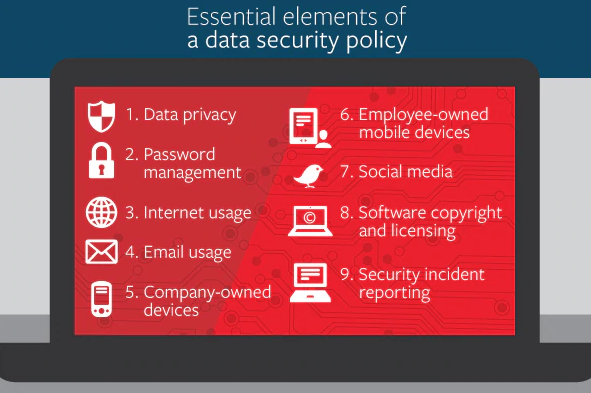
Essential Elements of a Data Security Policy
- Safeguard Data Privacy: Employees must understand that your privacy policy is a pledge to your customers that you will protect their information. Data should only be used in ways that will keep customer identity and the confidentiality of information secure. Of course, your employees and organizations must conform to all applicable laws and regulations.
- Establish Password Management: A password policy should be established for all employees or temporary workers who will access corporate resources. In general, password complexity should be established according to the job functions and data security requirements. Passwords should never be shared.
- Govern Internet Usage: Most people use the internet without a thought to the harm that can ensue. Employee misuse of the internet can place your company in an awkward, or even illegal, position. Establishing limits on employee internet usage in the workplace may help avoid these situations. Every organization should decide how employees can and should access the web. You want employees to be productive, and this may be the main concern for limiting internet usage, but security concerns should also dictate how internet guidelines are formulated.
- Manage Email Usage: Many data breaches are a result of employee misuse of email that can result in the loss or theft of data and the accidental downloading of viruses or other malware. Clear standards should be established regarding use of emails, message content, encryption and file retention.
- Govern and Manage Company-Owned Mobile Devices: When organizations provide mobile devices for their employees to use, a formal process should be implemented to help ensure that mobile devices are secure and used appropriately. Requiring employees to be responsible for protecting their devices from theft and requiring password protection in accordance with your password policy should be minimum requirements. Read More
Agribusiness Insurance

To succeed in today’s evolving agribusiness landscape doesn’t just mean knowing your farm, ranch, stable or vineyard. These days, it’s critical that you stay up-to-date on the risks that threaten it, and understand your options to protect it. From extreme weather to the revolution in AgTech, Travelers Agribusiness helps you navigate the sophisticated hazards of your industry. We offer broad property and liability coverages, risk-control services and claim support tailored to meet the specific challenges you face, and to help protect what you have worked so hard to build.
Our leading-edge industry insights and expertise, strength of coverage and the competitive advantage we deliver to our policyholders by keeping them ahead of emerging risks, are just a few reasons why Travelers Agribusiness writes more farm and ranch insurance, exclusively through independent agents, than any other insurance carrier.1 And why we’re the right choice to protect what matters most to you.
Lines of Business:
- Auto
- General Liability
- General Liability – including Personal Liability
- Property
- Umbrella/Excess
Who is this right for?
- Citrus growers
- Commercial growers and packers of agricultural products
- Cotton growers
- Estate farms
- Family farms and ranches
- Grain & field crop growers
- Horse farms
- Livestock, primarily cattle & sheep
- Vineyards
- Wholesale nurseries
- Wineries, including tasting rooms
What is Personal Liability Insurance Coverage?
Personal Liability insurance is about financial protection – for you and your family. The personal liability coverage within your homeowners policy provides coverage for bodily injury and property damage sustained by others for which you or covered residents of your household are legally responsible.
Personal liability coverage provides for a defense if you are sued, and can pay damages to injured persons up to the limit of liability.
For example, if someone falls down your stairs, or your child accidentally throws a ball through a neighbor’s window, breaking an expensive vase, you may be held legally responsible for the damages caused.
Many homeowners insurance policies provide a minimum of $100,000 in personal liability coverage, meaning the insurance company can pay up to that amount in total to injured persons per occurrence. If you feel you need more protection, higher limits are available. You can also purchase a personal liability umbrella policy if you think you need additional liability coverage.
Medical Payments
Another type of liability coverage in a homeowners policy is medical payments to others coverage. The homeowners, renters or condo policy generally can provide for the payment of necessary medical expenses for guests who are accidentally injured on your property. This is regardless of whether or not you are legally responsible. It also can provide coverage in other situations as well.
The minimum amount of coverage available is $1,000 per person. Higher amounts of coverage may also be available.
Preparing for the Risks of 3D Printing in Manufacturing
In applications ranging from the automotive and aerospace industries to healthcare, food and consumer goods, 3D printing can shorten development cycles, lessen time-to-market and lower the cost of traditional manufacturing. By 2020, the global market for 3D printing hardware, supplies and services is estimated to reach $17.2 billion.1
But while the technology’s potential to revolutionize manufacturing has been well documented, the risks are not as well defined. In some cases, 3D printing, also known as additive manufacturing, brings uncharted risks including cyber and intellectual property risks. Every party in a global supply chain should understand the liabilities involved in 3D printing and be prepared to minimize them.

“Should a 3D printed part or food cause injury or illness, it could result in a financially devastating lawsuit,” says Mike Thoma, Global Technology Chief Underwriting Officer at Travelers. “Therein lies the challenge: The field is so new, no one is sure how liable they really could be.”
Following are four key risk categories for 3D printing that technology companies should understand, and an illustrative risk scenario for each category.
Property Damage Risk
If a 3D printed object causes property damage due to a defect or a failure to function as intended, it could lead to a lawsuit. Any company or individual involved in the product’s manufacturing or distribution chain could find themselves named as a defendant. Read More
Cyber Risks and Your Business [Video]
Small and medium-sized businesses may be at the greatest risk of a cyber breach, and the least prepared to handle it. Having pre-breach services to help avoid a breach in the first place, and a cyber breach coach to manage the fallout, can be the difference in whether or not a company stays in business.